Cloud computing has transformed the business landscape, providing unmatched scalability, agility, and innovation. However, the benefits come with the challenge of managing and optimizing costs, especially in the ever-growing and complex cloud environment.
One of the foundational practices you need to implement up front is tagging policies.
The Crucial Role of Tagging in Financial Operations
Tagging in Azure is crucial in order to effectively manage your cloud resources. It enables you to label your resources in a logical manner, including individual resources, resource groups, and subscriptions. This systematic approach facilitates resource identification based on criteria set by your organization, enabling you to track, organize, and manage resources efficiently.
In terms of financial performance, tagging can help you manage and optimize costs in Azure by accurately associating resource usage and related costs with the specific people, products, and processes that consume them. Cost-related tags in Azure can support many different cost tracking and allocation requirements like show back and charge back.
Three commonly used tags are:
- cc - Charge Code or Cost Center
- env – environment (ex dev, test, uat, prod)
- owner – a user’s email, security group to distribution list
Striking the Right Balance with Required Tags
Some companies require many tags to enact firm governance. Other companies operate without any required tags. Neither approach scales well.
Here is a rule of thumb to use for required tags: Is the consequence of not requiring the tag far more costly than the overhead and policy to force people to supply the tags?
For specific apps, business functions consider scoping a special required tag policy to just that management group, subscription, or resource group.
The goal is to carry only the smallest number of required tags to minimize friction and maintain the cloud’s speed advantage.
|
Tag |
Consequence |
|
cc |
Show back and charge back of cloud costs becomes very difficult. |
|
env |
Implementing policies for production vs non-production becomes very difficult. Application teams knowing their development costs becomes harder. |
|
owner |
Tracking down incidents on resources becomes difficult. Distribution lists or security groups as the owner value is recommended. |
Resource vs Resource Group Requirements
One of the issues with Azure out of the box cost management exports is that the tags that are exported are at the resource or instance level. This forces you to enact tagging policies at the resource level if you want the out of the box reports to allow for proper allocation.
What ends up happening is users will either pick a random value or just make something up to get over this hurdle, especially if they are just working on a proof of concept. This “friction” inhibits cloud adoption at a minimum and corrupts the financial cost allocations at a maximum.
Instead, if we require tags at the resource group or subscription level and apply the notion of inheritance from resource group to resource and optionally from subscription to resource, we can remove the friction and still deliver fully allocated, accurate cost management reports.
To implement this, we employ a daily scrape of every subscription and resource group’s tags into a data store. We then join the tags with the costs that come in via their subscription + resource group to add the proper tags to the costs.
This approach also allows you to apply tags to all your historical data, even if they were created pre-tag policy and didn’t have them defined.
Required Policies
A proven practice to prevent the consequences of missing tags is to implement your required tag polices in your cloud landing zone upfront. Here is an example Azure policy that requires the env (environment tag) on resource groups with one of the valid values: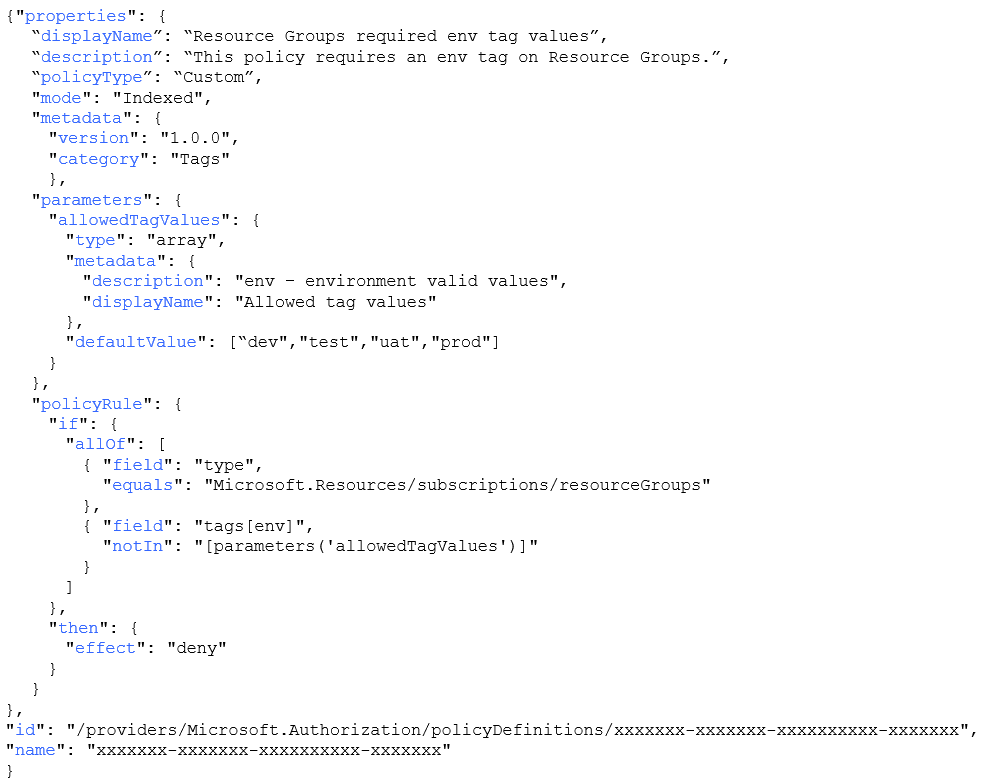
This policy restricts the env tag values for resource groups. You can specify the list of allowed tag values in the allowedTagValues parameter. The policy checks if the env (environment) tag is not one of the allowed tag values and will deny the creation of the resource group.
Mitigating Tag Sprawl
As organizations mature in their tag usage, tag sprawl becomes a common issue. This issue is exacerbated by tags with very large names and/or values. To address this, use concise and accepted labels and values when reporting, viewing, or managing tags. This approach mitigates the risk of tag sprawl and ensures effective tag management.
When reporting, viewing, or managing tags you should use the smallest well known and accepted labels and values as possible.
Conclusion
Proper tagging policies with a frictionless approach can transform financial operations into an asset for your enterprise.
Valorem Reply’s FinOps solution is a powerful way to manage your cloud costs and maximize your cloud value. By following the FinOps Framework and using the Azure tools and services, you can transform your cloud financial management and drive better business outcomes.
If you want to learn more about FinOps for your organization, ask us about our FinOps Accelerator and start gaining full control over your Azure costs.
Additional references:
1. Cloud Naming Convention: Consistent cloud naming strategy is the first step in achieving even basic levels of consistency and prerequisite to establishing any sort of cloud governance.
2. Tutorial: Manage tag governance with Azure Policy: This tutorial walks you through the steps of creating and applying a tag governance policy to your Azure resources, using the modify effect and remediation tasks.
